Deploy Synchronization Application (Customer Subscription)
This section describes how to setup and configure the App registration for the Background registration with a Customer Azure subscription. The App Registration manages the automatic synchronization between the Live Platform Multitenant Portal and the customer’s Microsoft 365 platform. You must add the App registration under the Provider Tenant’s Azure subscription for each UMP device. In this procedure, a redirect URL is configured which is used as part of the token authentication for requesting email consent from the customer tenant to connect to their Microsoft Office 365 platform (see Running Token Authentication Invitation Wizard).
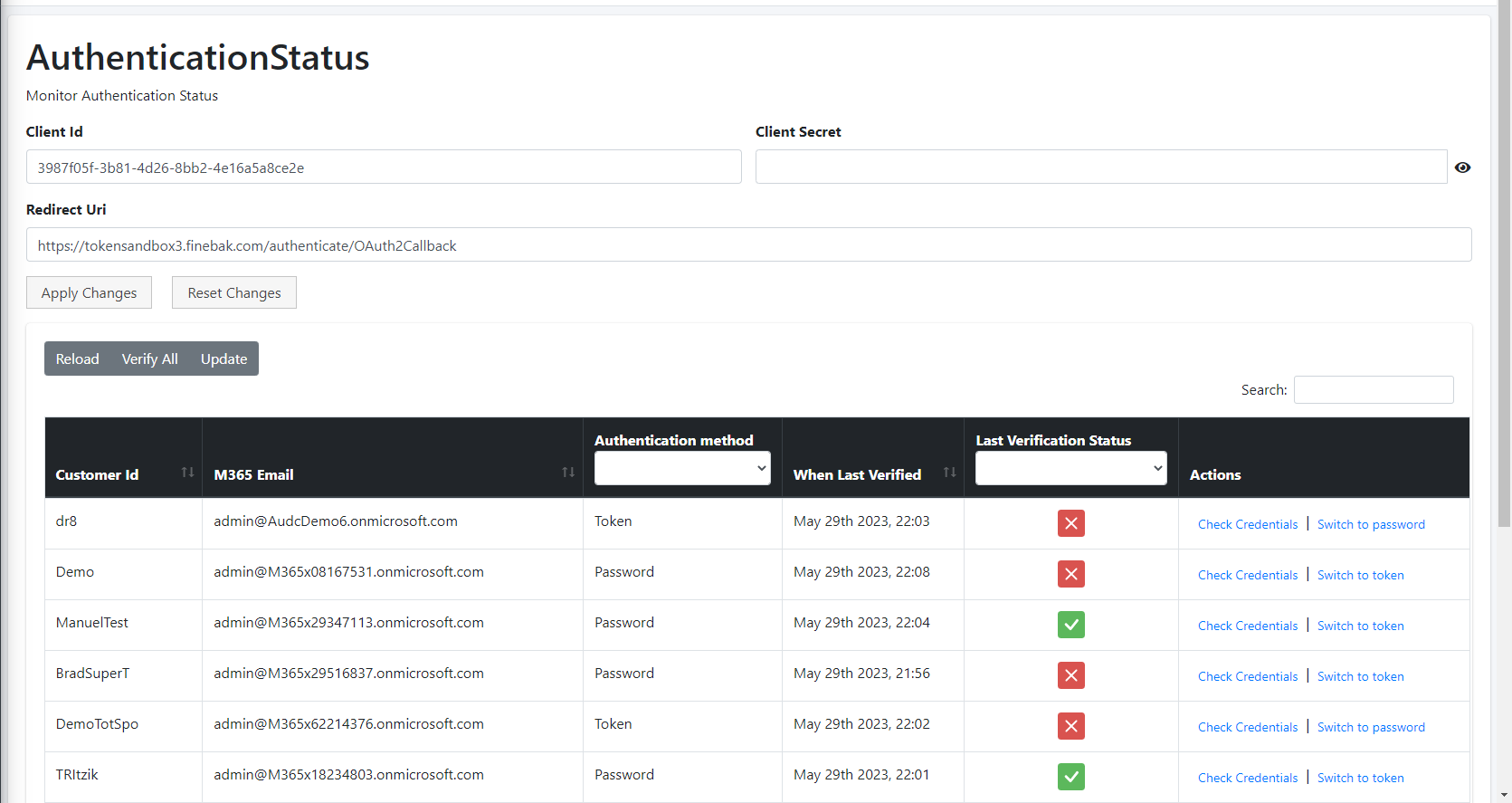
In this procedure, the Client ID and the Redirect URL must be configured in the Auth Tokens screen in the Multitenant interface (see Step below and Pending Invitations). Once this registration is finished, the details of the M365 user configured in this procedure are displayed in the Multitenant portal in the Microsoft 365 Settings screen (see Securing Microsoft 365 Service Provider Access).
Once you complete this registration, administrator roles must be assigned to the customer IT administrator who provides consent to Service Provider IT administrator for using the token authentication (see Assigning Administrator Roles to Customer IT Administrator).
|
●
|
If this procedure is performed by AudioCodes Professional Services, a Global-admin account should be provided by the managed customer. This global registration is used for all AudioCodes Live Direct Routing and Operator Connect customers. |
|
●
|
The domain names shown in the procedure below are examples only. |
|
●
|
For each customer, a unique redirect URL is defined. |
|
●
|
This procedure must be performed by new customers running a clean installation. For existing customers, the registration must be updated as described in Post Upgrade Actions. |
|
1.
|
Access the Provider Azure Active Directory admin center/ app registration on the Azure portal with System Admin permissions. |
|
2.
|
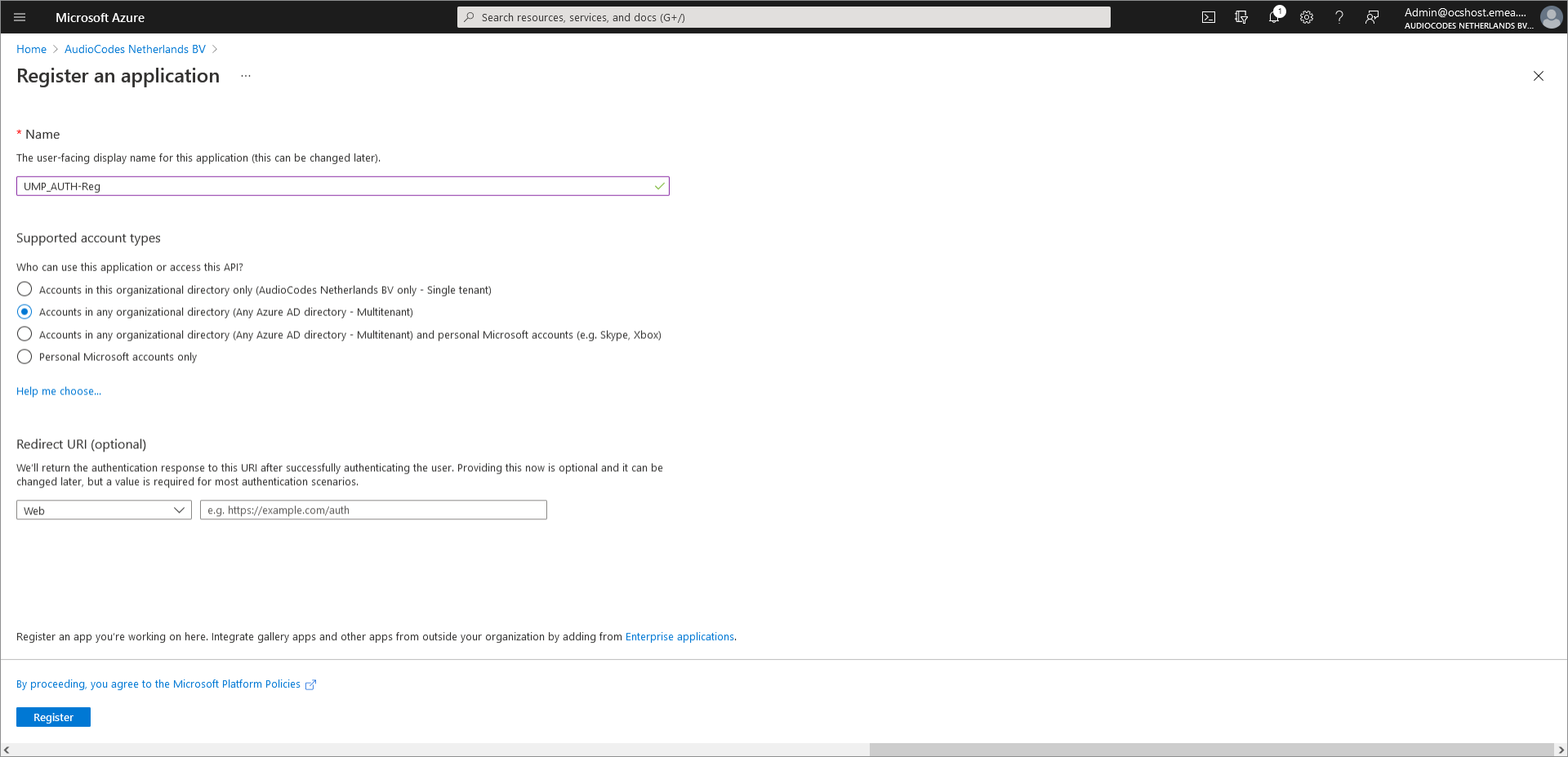
Enter the following details: |
|
●
|
Name: App registration name |
|
●
|
Select account type: Accounts in any organizational directory (Any Azure AD directory - Multitenant) |
|
4.
|
In the Navigation pane, select Authentication. |
|
5.
|
Under Platform configurations/Redirect URLs, click Add URI. |

|
6.
|
Enter the HTTPS URL of the UMP installation VM (e.g. https://livecloud.finebak.com/authenticate/OAuth2Callback) |
where:
|
●
|
“Finebak.com” is the FQDN of the Azure Virtual Machine where UMP is installed |
|
●
|
“OAuth2Callback” is the name of the token authentication page inside the registered application |
|
7.
|
Copy the URL to notepad as it is required later in the configuration. |
|
8.
|
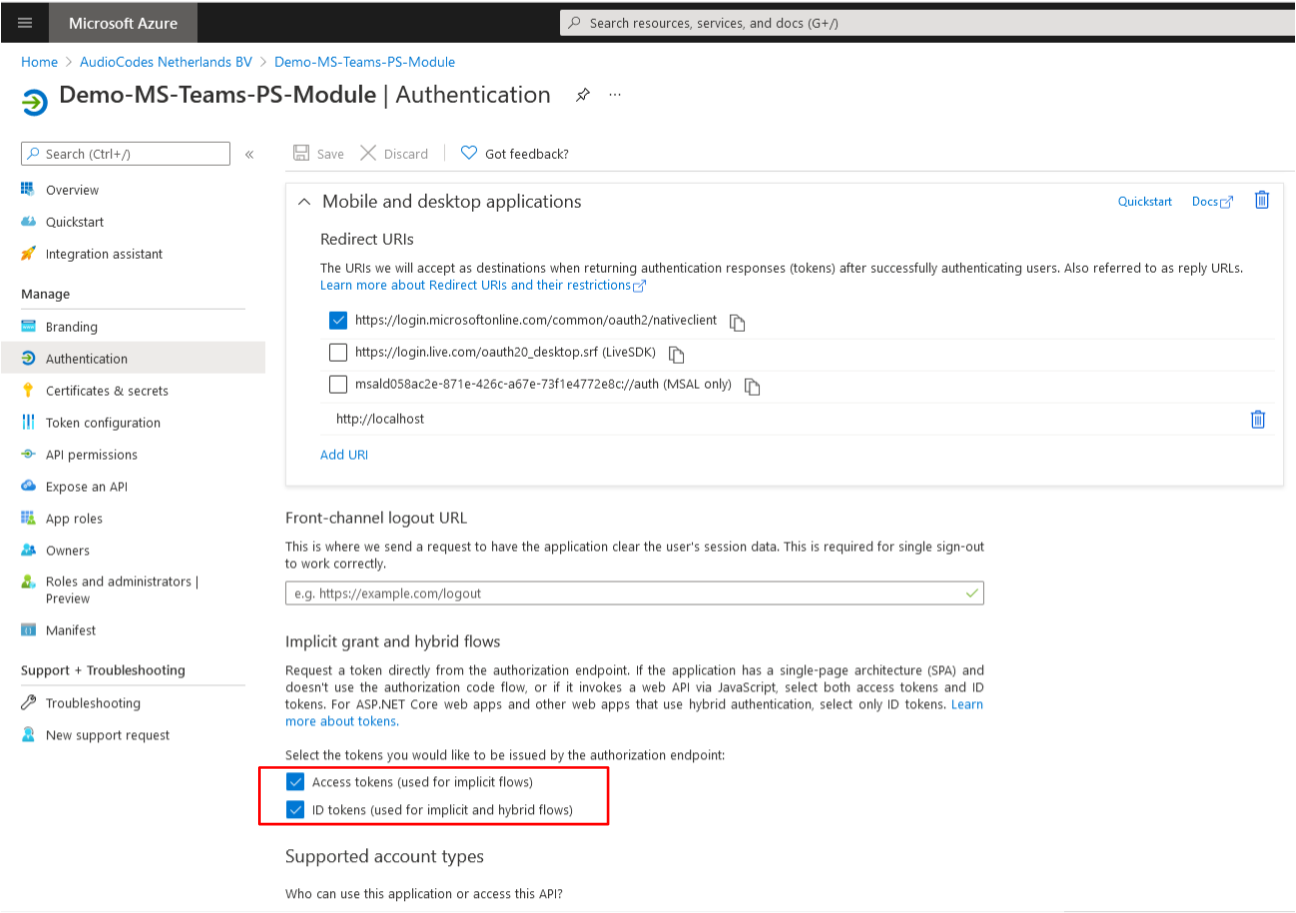
Under implicit grant and hybrid flows, select the following check boxes: |
|
●
|
Access tokens (used for implicit flows) |
|
●
|
ID tokens (used for implicit and hybrid flows) |
|
9.
|
Under Supported account types, select Accounts in any organizational directory (Any Azure AD directory – Multitenant). |
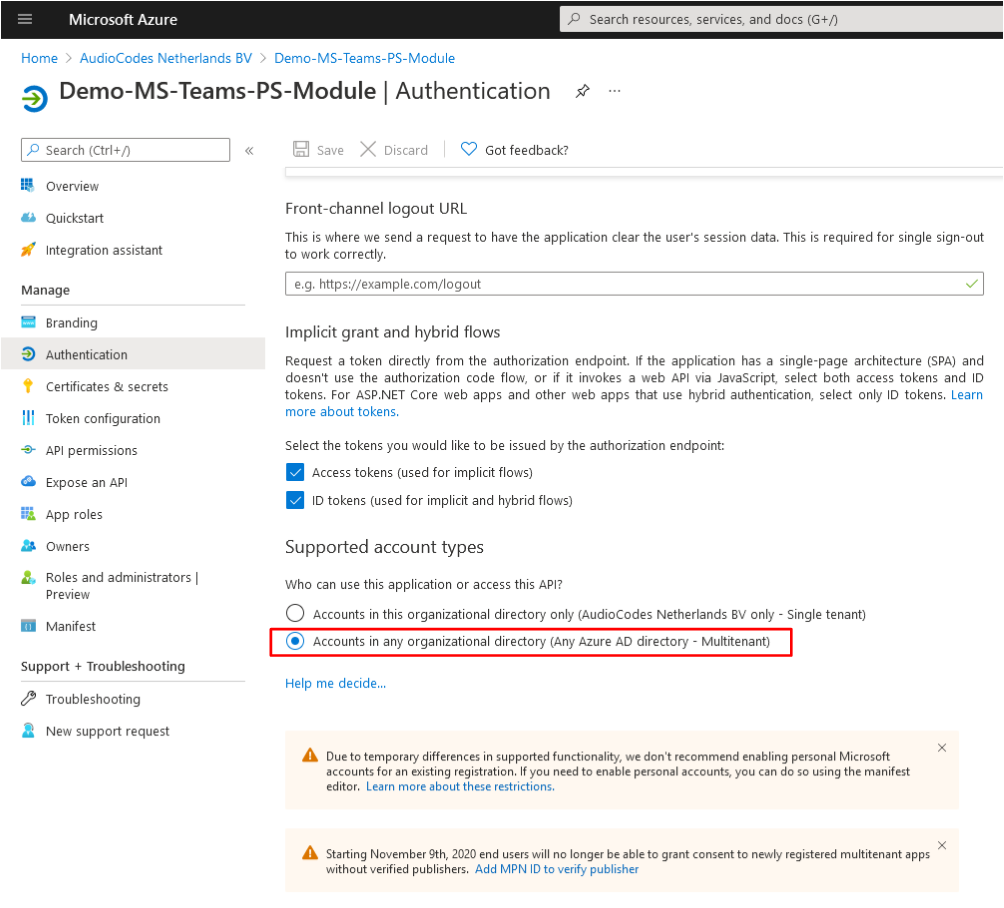
Verify the MPN ID to ensure that the Consent dialog will automatically be set as a trusted application.
|
10.
|
Under Advanced Settings, set to Yes. |

|
11.
|
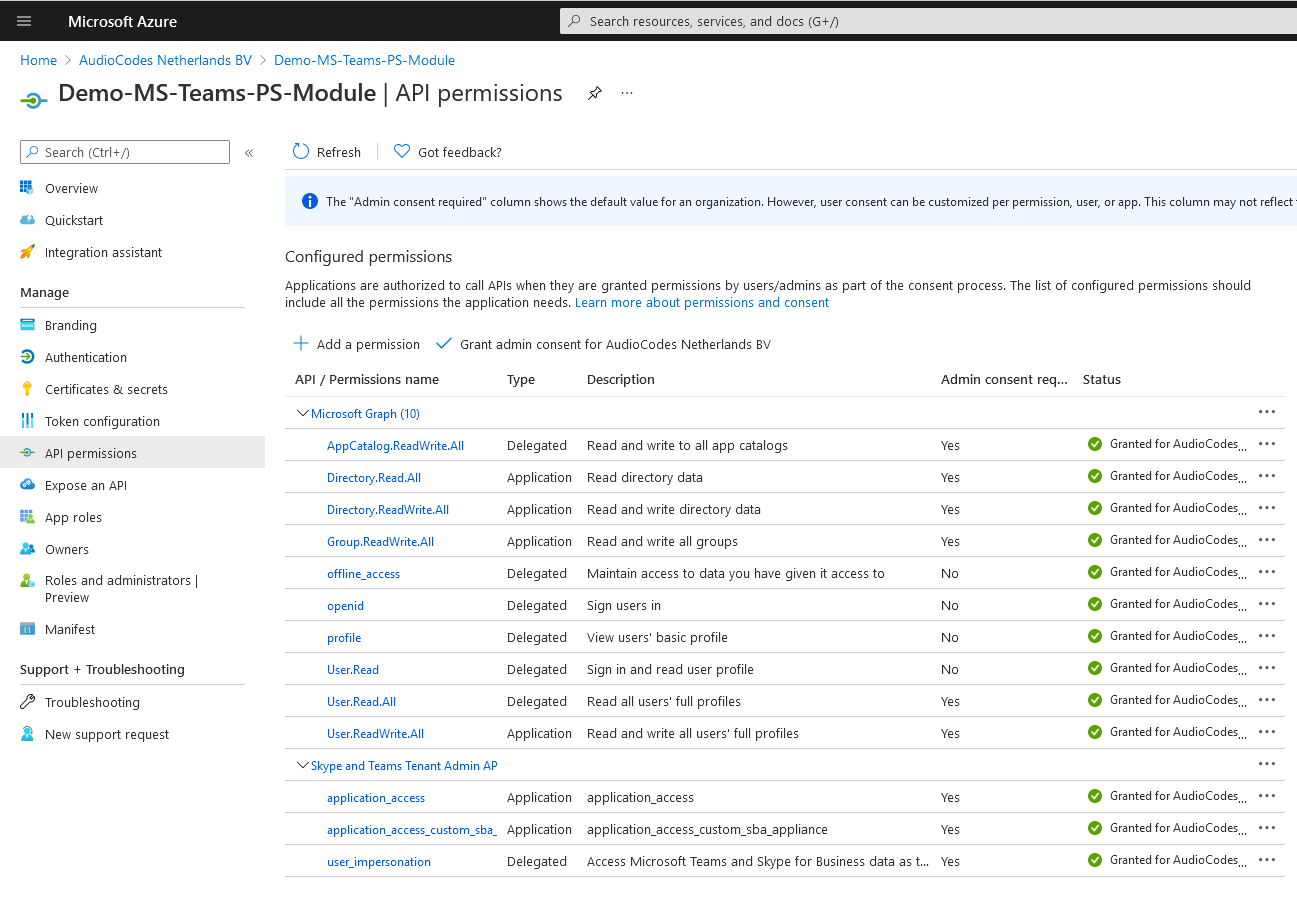
In the Navigation pane, select API Permissions. |
|
12.
|
Set the permissions shown in the figures below. |

|
13.
|
Navigate to the Overview page. |
|
14.
|
Copy the Application (client) ID value to notepad. |

|
15.
|
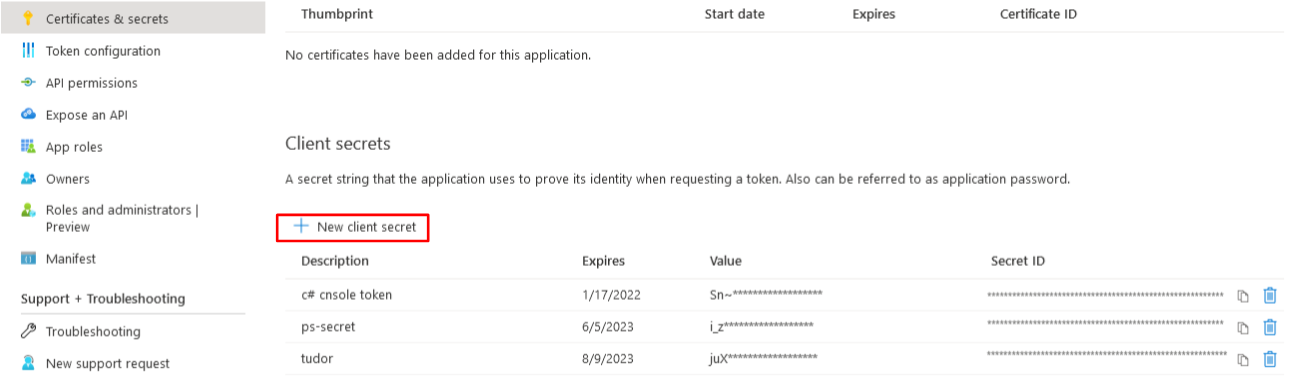
In the navigation pane, select Certificates & Secrets and then click New Client secret. |
|
16.
|
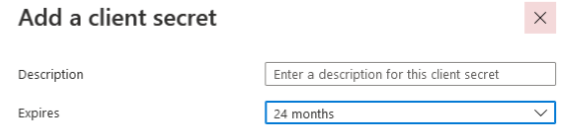
Enter Description, set Expires to 24 months and then click Add. |
|
17.
|
Copy the newly generated secrets’ Value to notepad. |
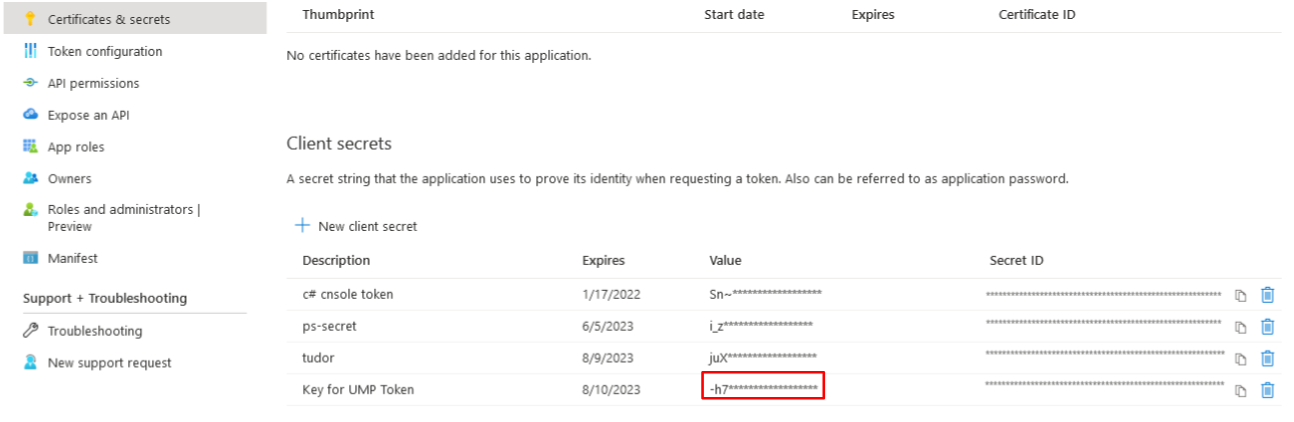

|
18.
|
In the Multitenant Navigation pane, open the Auth Tokens page (Security > Auth Tokens) and do the following: |
|
●
|
Paste the Application (client) ID and Client secret value to the respective fields. |
|
●
|
Enter the RedirectUrl that you configured above. |
For example https://livecloud.finebak.com/authenticate/OAuth2Callback